Intro
Welcome to Just a Tech Geek, JATG, I’m your host Justin! Thank you for listening today!
First, let me paint a word picture and setup today’s topic:
It happened again, another major company had a data breach. What is this, like the 10th time this month some major company had a data breach? Great… now it’s time to figure out if my data in this breach. Let’s go heck out haveibeenpwned.com… Well shoot, my email AND my phone number were in that breach.
What do I do now, and how can I stop this in the future?
Well in today’s episode of, Just a Tech Geek, we are going to talk about this! What are passwords, how can you keep your accounts as safe as possible, and the future of passwords (here’s a hint, they’ll eventually be going away BUT it will take some time.)
About Passwords
Passwords are complicated, but they’re a necessary evil for the time being.
Passwords exist in order to identify who you are and the data that exists that belongs to you. It will essentially say, HEY I’m Justin (aka your username) and you verify or validate this by confirming the secret handshake (aka password) that you setup when you created an account. So in order for a website, or app (which is really just an extra fancy website at a certain point) to validate who you are you need to PROVE you are who you say you are.
This is the reason why we have passwords BUT honestly passwords aren’t the greatest. There are so many services/accounts/apps that we use in our day to day lives, that it is difficult to create a unique password for every single one. Sometimes those accounts only prompt you once every few months to sign in again. So what was that password you used months ago that you have no muscle memory for? Right? These things are a ROYAL pain but there are some tools you can use to help you manage all these passwords AND there’s other ways to secure those special accounts that are extra sensitive.
Best Practices
The Toolbox
So you hear that there are tools that you can use? GREAT! Why would you trust them, and how do they make your life ACTUALLY easier? You can easily use your phone, computer, or tablet if you are on an Apple product. Today I’m going to really be focusing on Apple Products, and some cross platform tools you can use because I’m most familiar with these products. I apologize if you’re not an Apple fan or their products aren’t for you… but I will hit on some tools that I use on my windows computer in conjunction with my Apple products (there’s hope!)
Apple Products
Apple products are pretty damned expensive, that being said they have some benefits to using Apple devices in conjunction with Apple’s iCloud service. One of the greatest benefits is that Apple can securely save your passwords, 2 Factor Authentication Codes, and even more!
Through the power of math, and being one of the richest companies in the world with some EXTREMELY talented developers, Apple saves your password in their iCloud service in a way that only YOU can get access to this information. These are some gotchas when it comes to this, but Apple has designed their system to mitigate as many gotchas as possible.
Some of Apple's Mitigations
Apple goes out of their way to secure your data, which is great. Admittedly they aren’t perfect or even the best with everything, but they do tend to think about security as much (if not more) than other companies. For example, on most (if not all modern apple devices) they have biometric authentication. They will REALLY push you to setup FaceID or TouchID, and that’s a good thing AND you should ALWAYS just set that up. Once that’s setup in order to get access to any password on your device a person would need to: Know your Apple device’s password, know your AppleID’s password AND would need to have your face/finger. Sort of a pain for a bad actor if you ask me.
A note about setting up FaceID/TouchID. Apple, the company, doesn’t do anything or even has access to your Face or Fingerprint data (which is more than what other companies/governments do). All of that data is processed and stored in your device on their T series chips (You can read more about their latest T Series chip, the T2, chip at Wikipedia) and for the most part REALLY can’t be extracted out of your device.
So when in doubt, let your iPhone create a password for you when it prompts you. Usually your phone will prompt you to generate (or even save) a username/password in websites and most apps. If it doesn’t prompt you, you can add it in manually by going to Settings → Passwords. Something else that’s pretty cool, is that your Apple devices will also remember 2 Factor Authentication (2FA) codes too! Try either right clicking or long holding on a QR Code for 2FA setup. There should be a setting to remember them. If not, you can also manually add in the 2FA code to an existing password! Just copy the setup code, open up Passwords in Settings and find your exisitng account and click Set Up Verification Code on your phone/tablt or Set Up... under Account Options → Verification Code.
FINALLY the coolest thing that Apple added in late 2022 is the ability to access these Passwords on your Windows device with the iCloud app! Granted the app isn’t super well reviewed in the Microsoft Store but I’ve used it and it works pretty well! Heck it’ll even do auto-fill in Chrome or Edge! Not too shabby!
Caveats for Apple Device Generating Passwords
Some Caveats to your Apple Device Automatically Generating Passwords
Unfortunately apps aren’t always coded in a way to hint to your Apple device that it’s prompting for a username and password so sometimes you might need to go into Settings → Passwords to manually generate a username and password. YOU SHOULD DO THIS! This is super helpful and Apple will generate a good password for you. The most important thing is probably to just have a unique password for each app/web service so that if one of them does end up getting compromised at least it lowers the liklihood for another account (with potentially even more sensitive information) being compromised.
Sign in With Apple (or Google / Microsoft)
Something newer that Apple has started presenting users with (via an admittedly strong armed method) is an option to Sign In/Up with Apple! This is a neat, and pretty secure way, to Sign Up and Login to Accounts!
What it does is that it uses your web browser (so Safari or Chrome) to ask your phone to verify who you are, and then tells the website or app that you are who you say you are. It’s a solid way to sign up for services, especially if you’re using the default Safari/Apple product combo.
The Apple Combo for Sign in with Apple
When you use an Apple device in conjunction with Safari the website will ask Safari to verify who you are, Safari will in turn ask your Apple Device. Your Apple Device will do a FaceID/TouchID/Password verification and will tell everyone down the chain will receive a validation (from up the chain) that you are who you are from when you signed up for the website or service.
Here’s a VERY GENERIC Sequence of what Happens
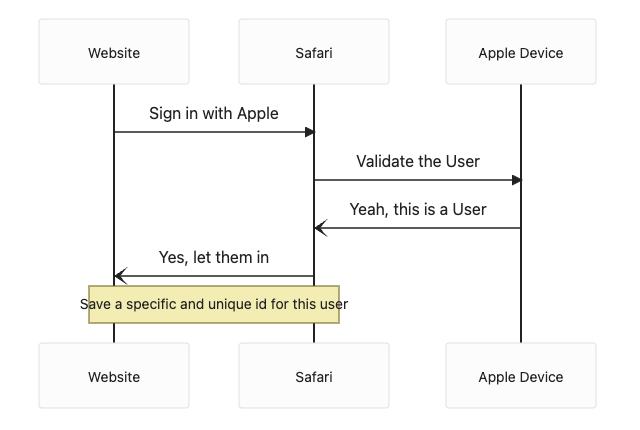
Password Managers & 1Password
Something else you can use, either in conjunction with your Apple device (or in place of it) is a Password manager! This isn’t a bad recommendation at all, but I do want to make something VERY CLEAR. You still need to remember one REALLY GOOD password. So nothing like your nickname, or anything like that, use something more complicated so that people REALLY can’t guess or brute force your password.
There’s a good cartoonist by the very nerdy comic writer xkcd about Passwords. They show a pretty good option for making a super solid password, which is a long and silly sentence (or maybe a reverse Acronum – So
ThingReallyIsn'tANounGoshLeaveEverything1! for Triangle.
Btw, don’t use that as a long password 
Regardless something like 1Password is great because it’s considered pretty darn secure based off what security experts say (they require three things to validate who you are, and potentially 4 if you set up 2 Factor Authetication). So their architecture is better than Lastpass which has had their fair share of issues as of lately, including their parent company LogMeIn. You can setup user names, passwords, 2FA, and so much more!
The best part is that you can use it on virtually any platform – iPhone, Mac, Windows, Android, even your favourte Browser! It does cost monthly/yearly, but I think it’s a worthwhile investment in your security!
Extra Security
2FA or 2 Factor Authentication
Now you might have heard about this thing called 2 Factor Authentication and wondered… what and WHERE in the world is 2 Factor Authentication (sometimes called 2FA)? It is a second way to make EXTRA sure that when you show who you are, that there’s something else (unique only to you) that can be used to validate who you are. So in the example of the secret handshake, maybe there was something else you showed to the person when you did the handshake… maybe a special ring that leaves a unique design that can’t be copied or created by anyone else. This special ring is a decent, albeit rough, analogy of what’s happening.
The goal of 2FA is to use a method to verify that you are who you say you are by using something tangibly connected to you. Sometimes this is embodied by using a phsyical electronic key that can be linked to your account, other times it’s your phone number that an app or website will use in order to “challenge” that you are who you say you are by asking for you to reply with a code.
2FA in conjunction with username + password, is a great way to secure your accounts. That’s because if someone ever does get access to your username and password, they still need to use one more item, that’s tied to you in the phyiscal world, in order to validate you are who you say you are.
That being said, there are differen ways to do 2FA. In doing some research, there is sort of a priority list of what’s the best in terms of 2FA. Something to note is that this priority list is just something that I’ve come up with. This might not be PERFECT but I think it’s better than nothing.
- The Gold Standard
Username + Password + Physical 2FA Key (a product example is a Yubikey, or even your phone if you have an iPhone!) - The Steel Standard
Username + Password + 2FA App (for example Google Authenticator, Microsoft Authenticator, your iPhone, or Authy) - The Bronze Standard
Username + Password + 2FA Text Message
All three of these JATG™️ (that’s me) Standards are way better than just using your Username + Password. However, if you’re serious about security or are potentially at risk from being hacked then I’d highly recommend Option 1 – Username + Password + Physical 2FA key. That is really the best way (other than using a Passkey, more on this in a bit) to secure your account to a variety of attacks. What’s really cool, and unique, when it comes to using something like a 2FA Key (or using your iPhone as a 2FA key) is that the specific 2FA method is linked ONLY to that account for that website or app! So even if a hacker got into EVERYTHING (or the developers did a really bad job following best practices) the best they can do is get accesse to just that account… nothing else!
Using your phone as 2FA?!
Yes, you heard me right! You can use your iPhone as a means to do 2FA with web apps! This is sort of linked to the idea, and technology, of Passkeys. Essentially your phone is able to do enough of the SUPER DIABLO EXTRA SPICY 🥵 Math to ensure that you’re secure! So when you go to Enroll in 2FA, your Mac (or iPhone) will prompt you to use your security key to link your account to the 2FA method. When that prompt comes up, it’ll ask if you want to use your phone OR use a security key! Good on Apple!
The Future of No Passwords – Passkeys
I’m sure you’re listening or reading this and wondering… WHY THE HECK do we even need to use Usernames + Passwords if our devices can do so many cool math things to prove who we are! That’s a great question, and a very similar question to what big companies like Apple, Mircrosoft, and Google have asked. Together, and really led by Apple, they have made this standardized process that works across ALL (yes all, including Chromebooks) devices! It’s amazing!
The way the technology works is the coolest, or spiciest, way of doing math too! Essentially when you sign up for a website or app the website or app can setup a passkey to validate who you are. So when you go to setup the Passkey you’re able to link your specific account with a secet “key” that’s kept in your phone SPECIFICALLY for that app/website! That’s right this uses something called public private key encryption!
What is public private key encryption, you might ask? Great question! Realistically you don’t need to know the specifics of how it works, BUT what it’s doing, at the heart of this encryption methodology, is making a key and a lock. The key is your private key. This is something that should be GUARDED and NEVER given away. The lock, or public key, is something that anyone can use or have. It’s a unique mathematical lock that can only be unlocked with one key, and only one key! Which is pretty darn cool! That means anyone who has your public key can encyrpt something and only you can decrypt it with your private key!
Another Anology for Public/Private Key Encryption
Another fun way that I’ve heard this described is making up a private color. A great video, though it might be a bit techincal, is on a Youtube channel called Computerphile! That video is here!
Essentially try to imagine that when you’re making a public private keypair what you’re really doing is making a secret color that can only be known by you. So when you’re making the public/private key what you’re doing is splitting the secret color into two unique colors that make the secret color. There’s your secret color, and the color that EVERYONE can know about. Through the power of math, and maybe pigment technology, you
Going back to passkeys, what’s happening in the background is that the website or app is talking with your device and seting up a public/private keypair that can only be used for that specific website or app! That key is automatically handled by your device so that when an app presents a login screen your device will, securely, lookup any key that might exist for that app/website and will ask the app/website to furnish the public key. The device then checks to see if the public key is the one that’s specifically paired with the private key that it has stored securely. If they match then your device tells that app/website that you are who you say you are and to just let you in! Pretty amazing, huh? This is really the future. Websites and apps are slowly going down the process of implementing this technology. So give it a couple of years before you see this everywhere. That being said, some websites or apps will present you with the option to use a Passkey! If you’re feeling extra special, why not try it out?
Well thank you for listening / reading! If you do have any questions please feel free to reach out! I’ll do my best to answer any questions! I’ll do my best to reply, and if there’s a repeat question I’ll update my post with some FAQs. Thank you so much, and I hope you had fun listening/reading and learning something new! Now go impress your freinds!